BYOK with GCP¶
How to configure Bring-Your-Own-Key encryption with Google Cloud KMS?¶
Create GCP KMS Encryption Key¶
This section explains how to create a cryptographic key in Google Cloud KMS and grant access to this key to Afi Backup application. The guide assumes that you have a Google Cloud Platform account with enabled billing.
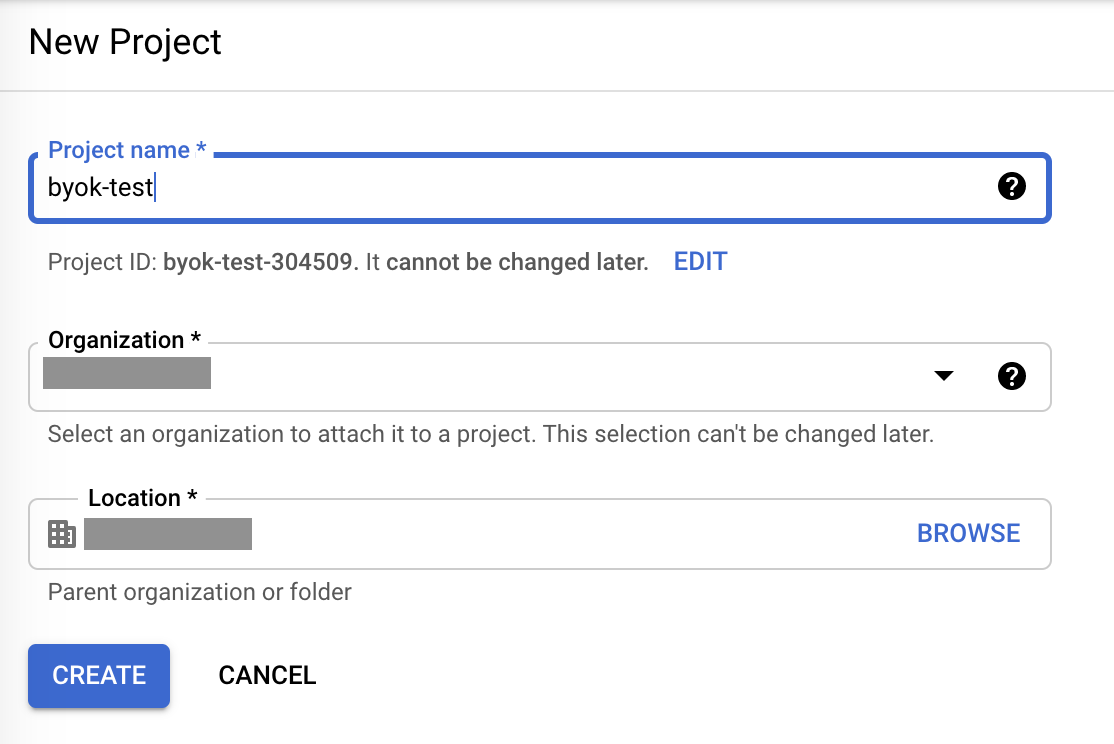
Step 1 - Create a new project in your GCP organization (for example, afi-backup-byok).
You can also use one of your existing GCP projects, but it can make controlling your GCP resources more complicated.
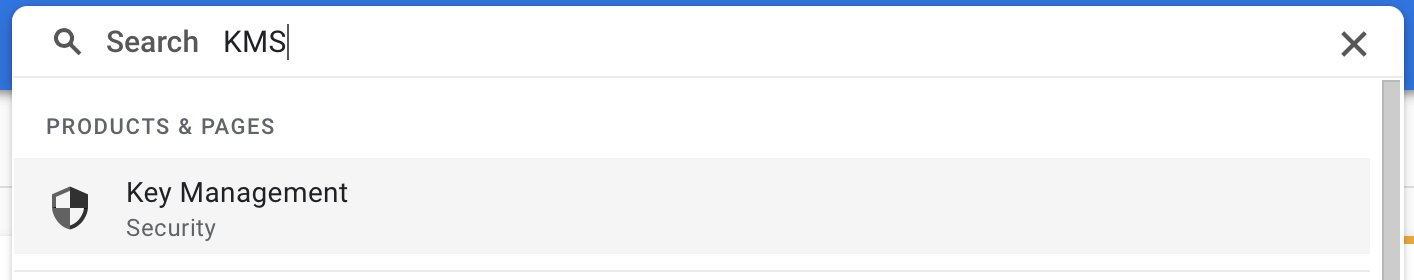
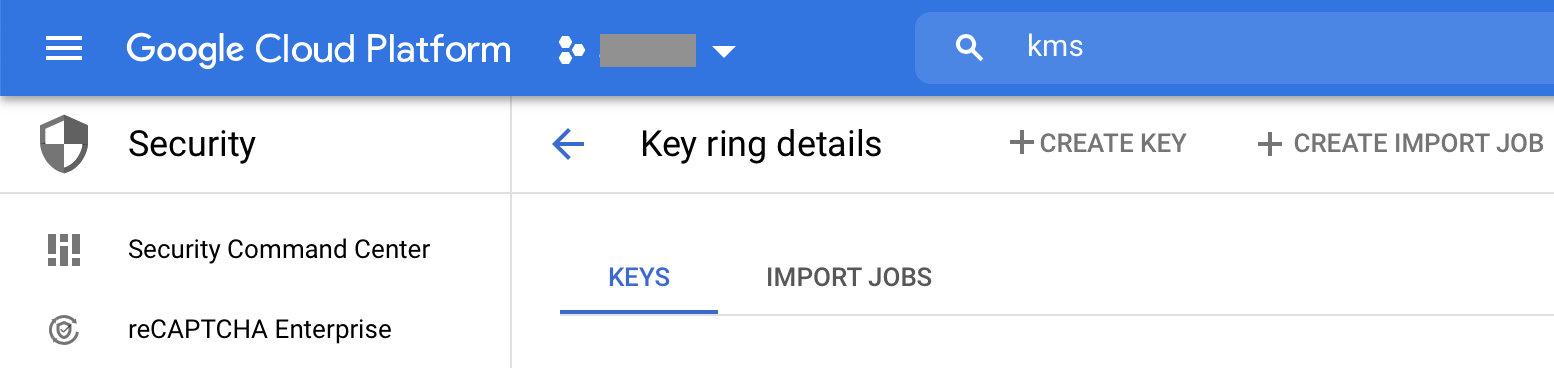
Step 2 - Go to Key Management (KMS) in the selected GCP project and enable Cryptographic Keys API if it isn't enabled yet (type KMS in the search field at the top of the screen to locate it):
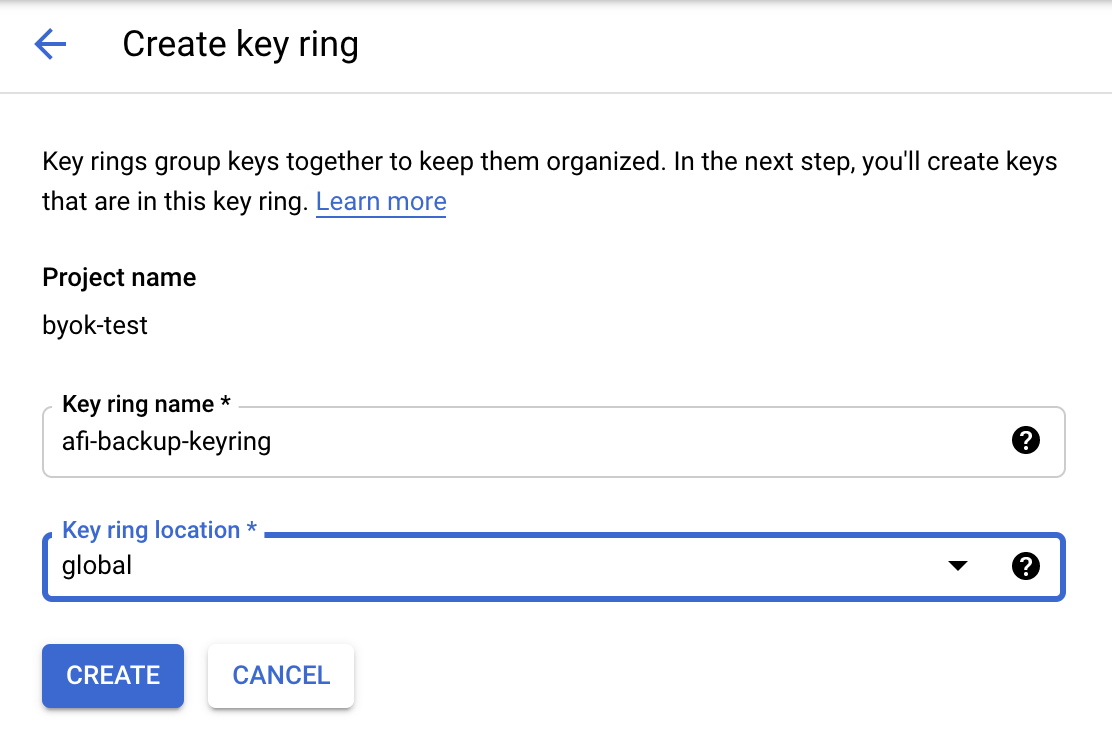
Step 3 - Create a new Key ring (for example, "afi-backup-keyring") with a "global" location. You can also specify the exact region where you want the key to be stored if you have such preferences.
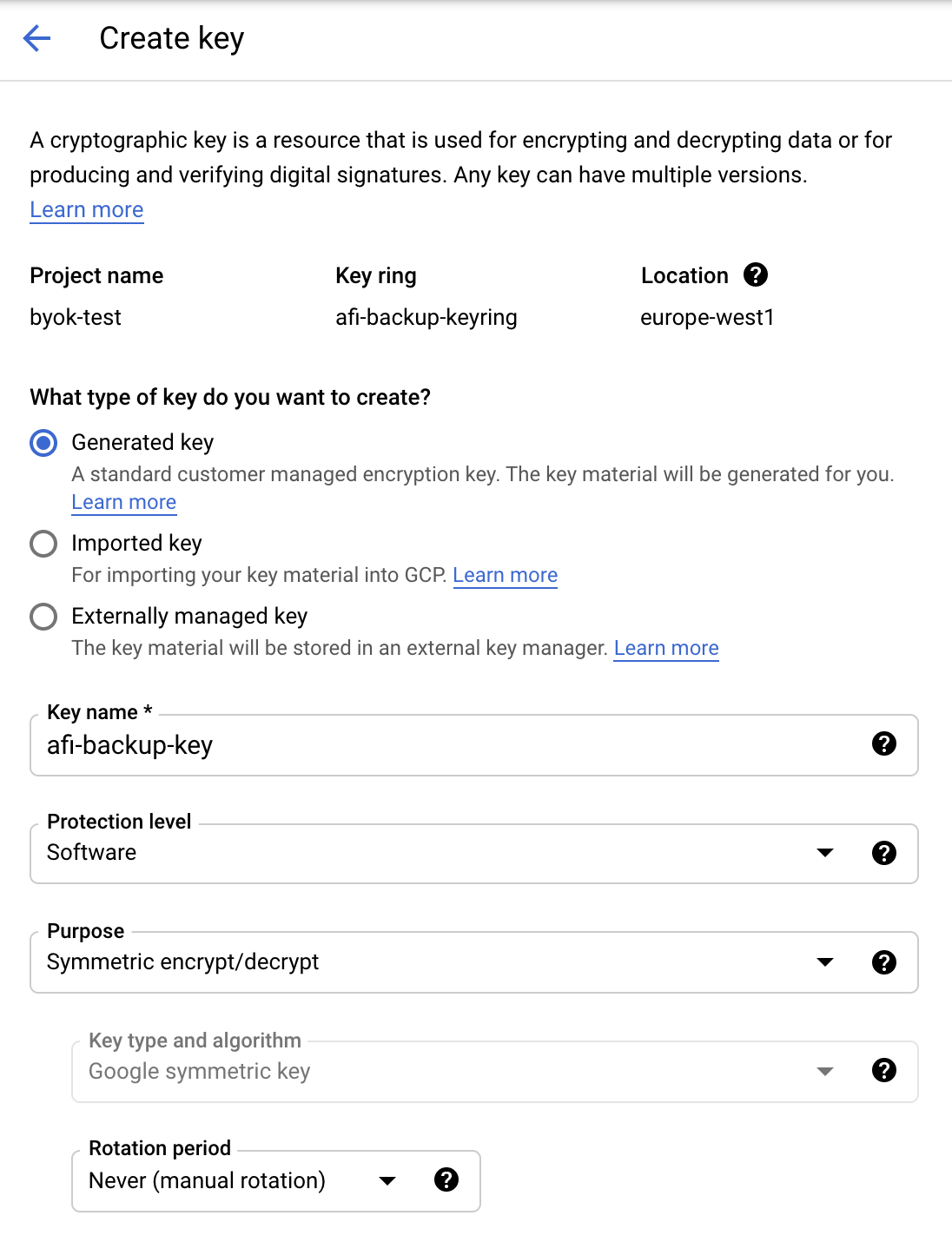
Step 4 - Click on the Key ring from the previous step and create a KMS key there (for example, "afi-backup-key").
This screenshot shows the recommended settings for an encryption key:
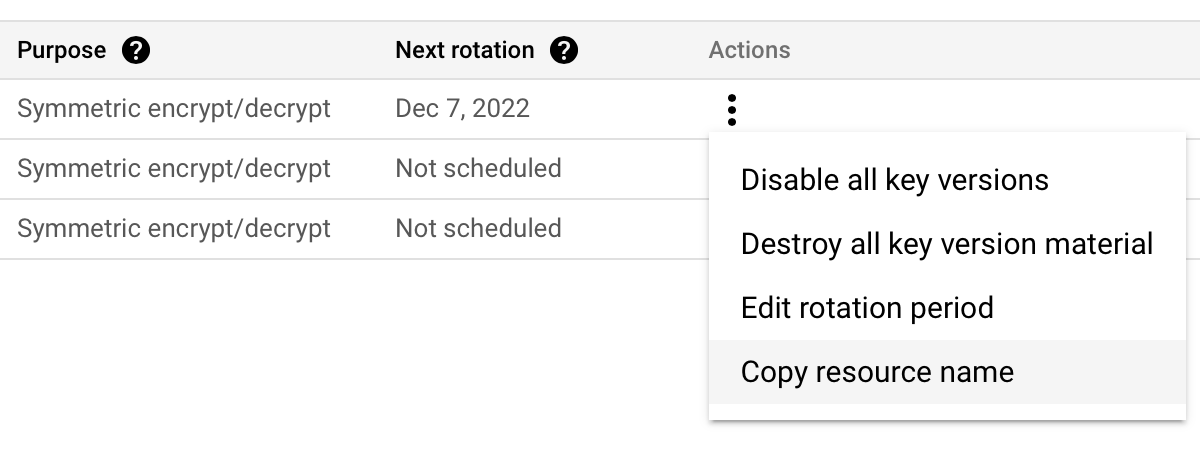
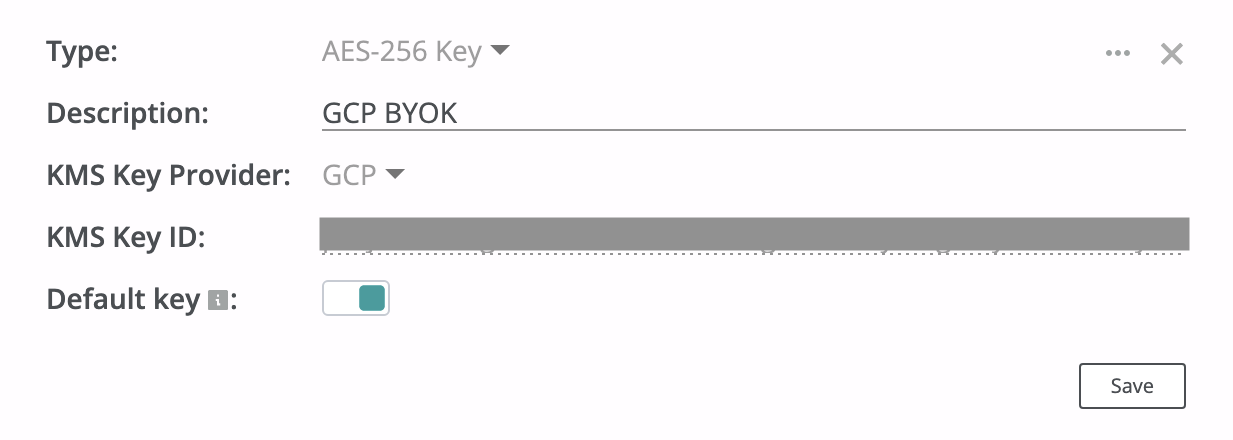
Step 5 - Copy the key name by clicking on Copy Resource Name. This key name should be used in Step 7 to finish BYOK configuration on the Afi side (key name example - projects/byok-test/locations/europe-west1/keyRings/afi-backup-keyring/cryptoKeys/afi-backup-key).
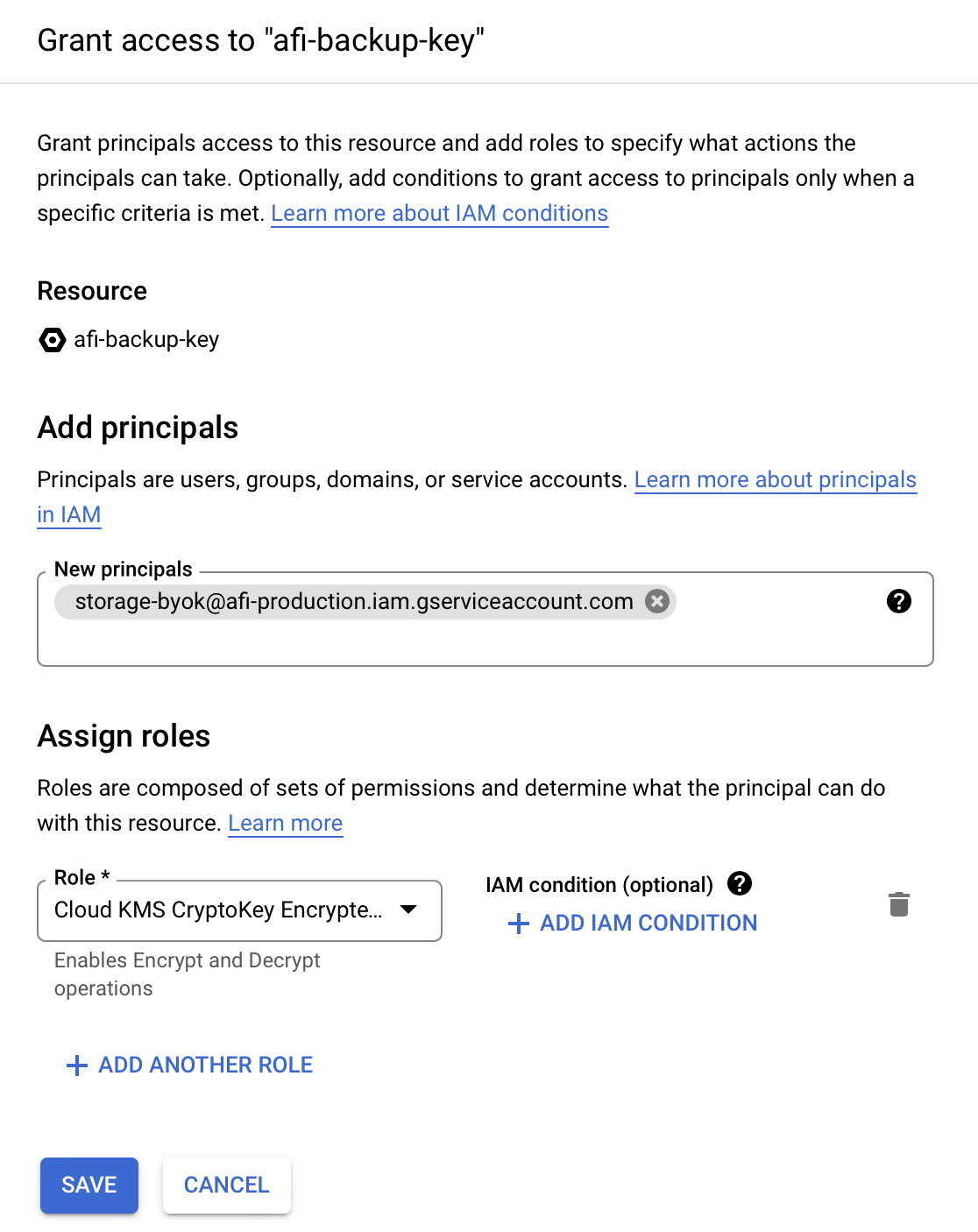
Step 6 - Open the Permissions tab for the key and grant access for the Afi service account (storage-byok@afi-production.iam.gserviceaccount.com) with a Cloud KMS CryptoKey Encrypter/Decrypter role. If the Permissions tab is hidden, click on 'Show Info Panel' in the top-right corner of the page.
Create Afi encryption key protected with GCP KMS¶
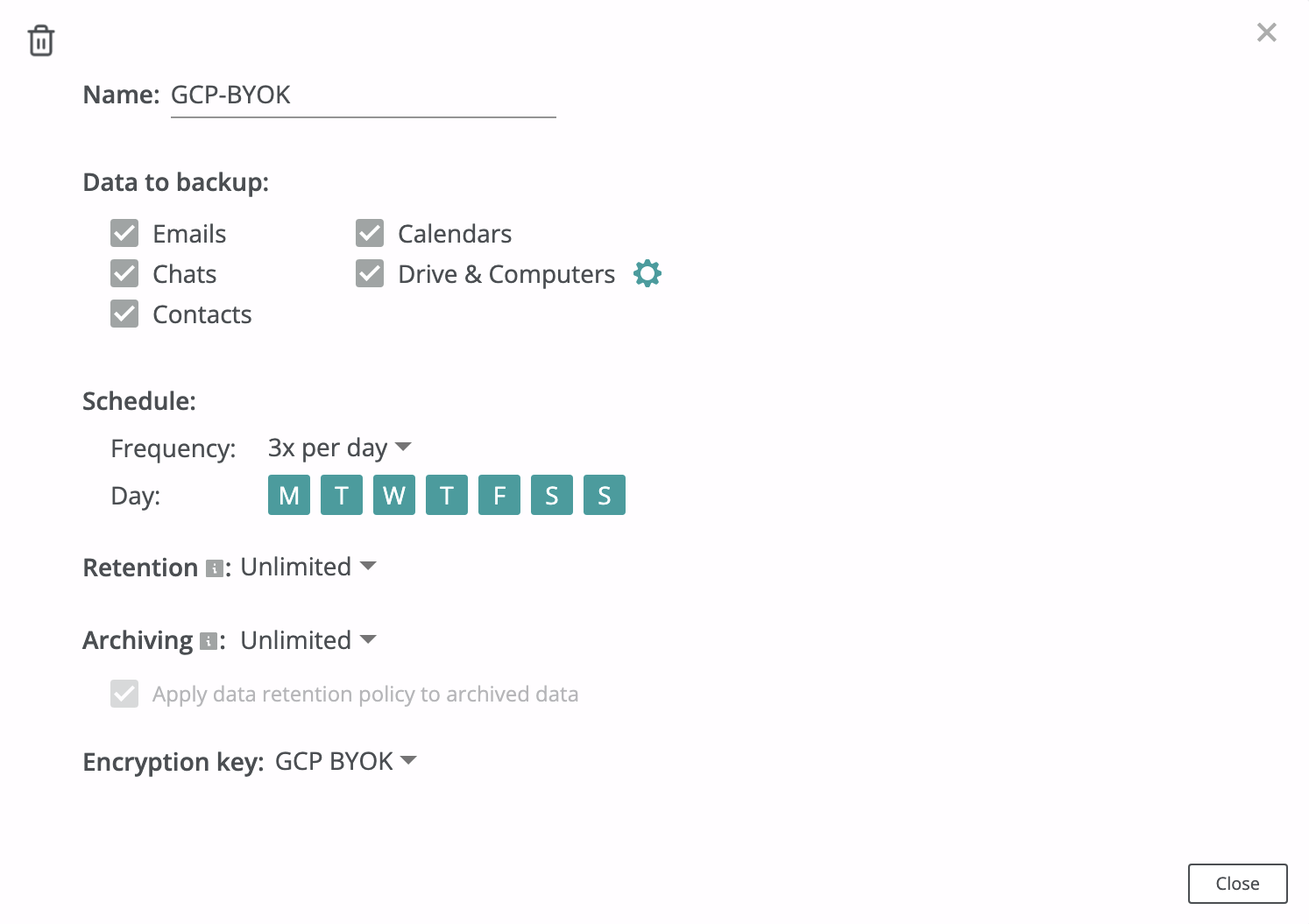
Create a GCP KMS key secret (use the key's Resource Name from Step 5 as the Key ID) in the Afi portal on the Service → Settings → SLA tab and select it as an encryption key in your backup policies.