Ingesting audit events to Splunk¶
This article explains how to create a Splunk log ingestion channel for Afi audit logs.
To create a Splunk HEC (HTTP Event Collector) collector for log ingestion, please do the following:
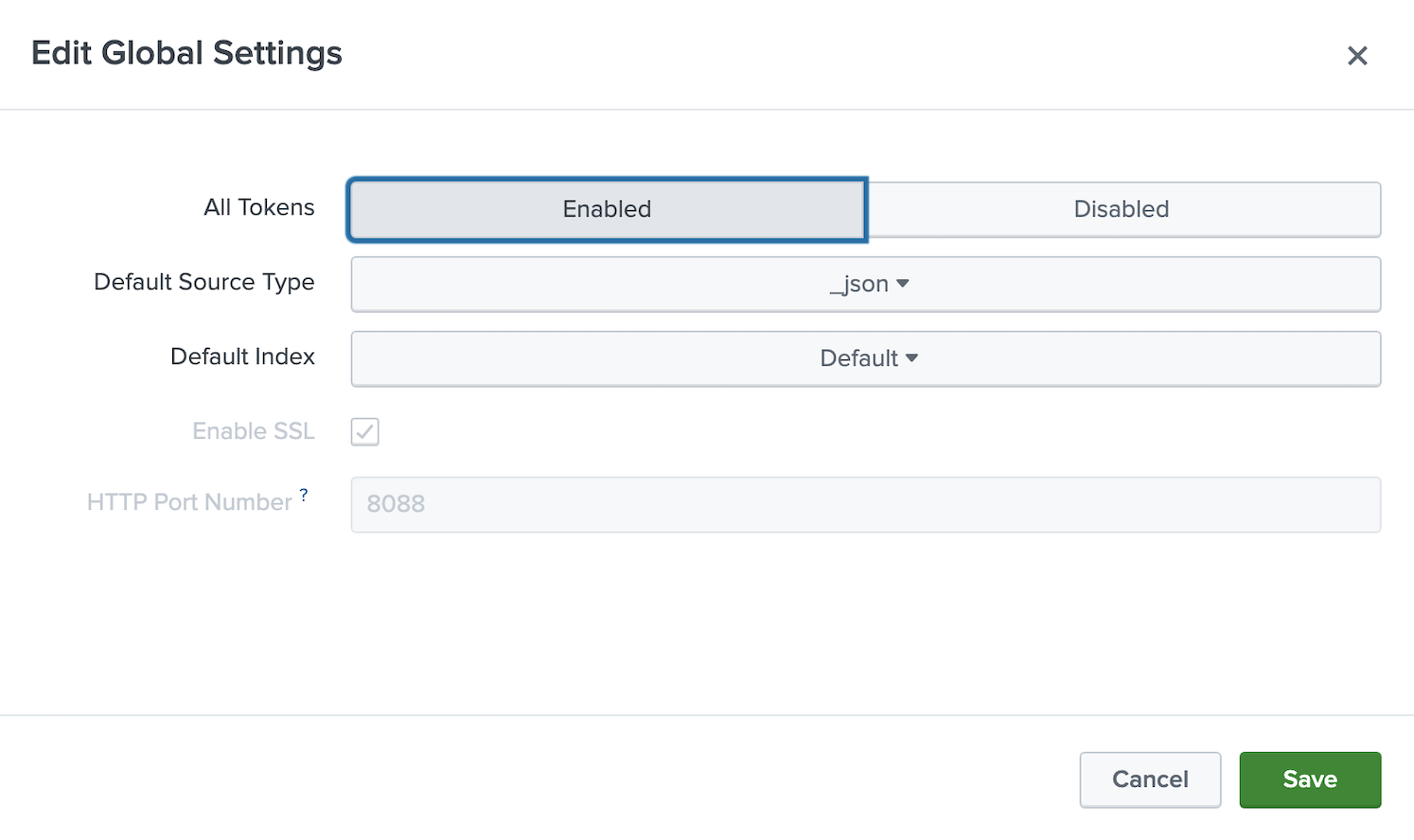
Step 1 - Go to Settings → Data Inputs → HTTP Event Collector in the Splunk admin panel and enable HEC by setting All tokens to Enabled in Global Settings. Also, choose _json as the default source type since Afi sends audit events in JSON format.
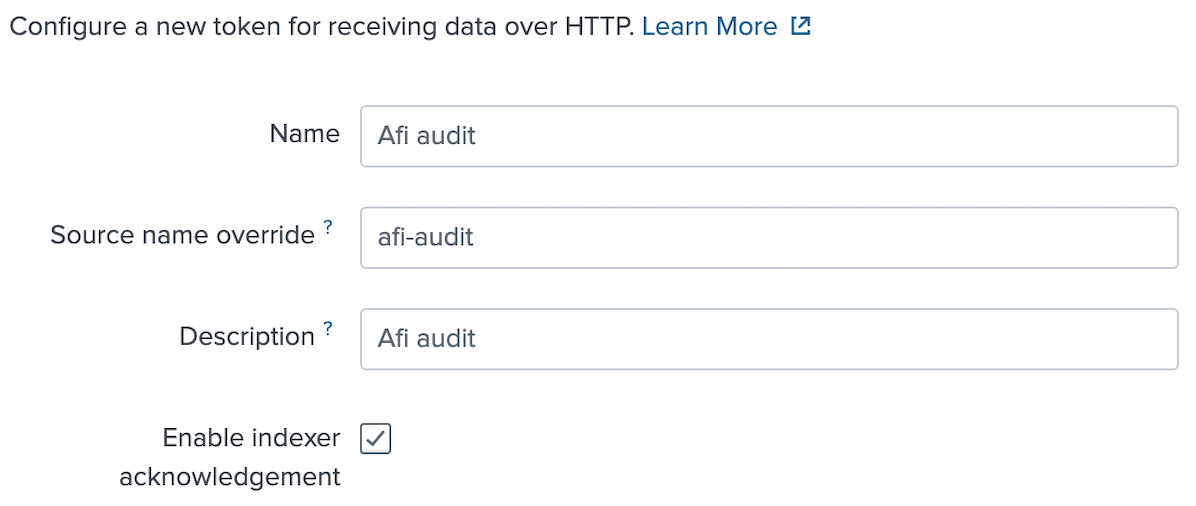
Step 2 - Create and copy a new HEC token by clicking on the New Token option.
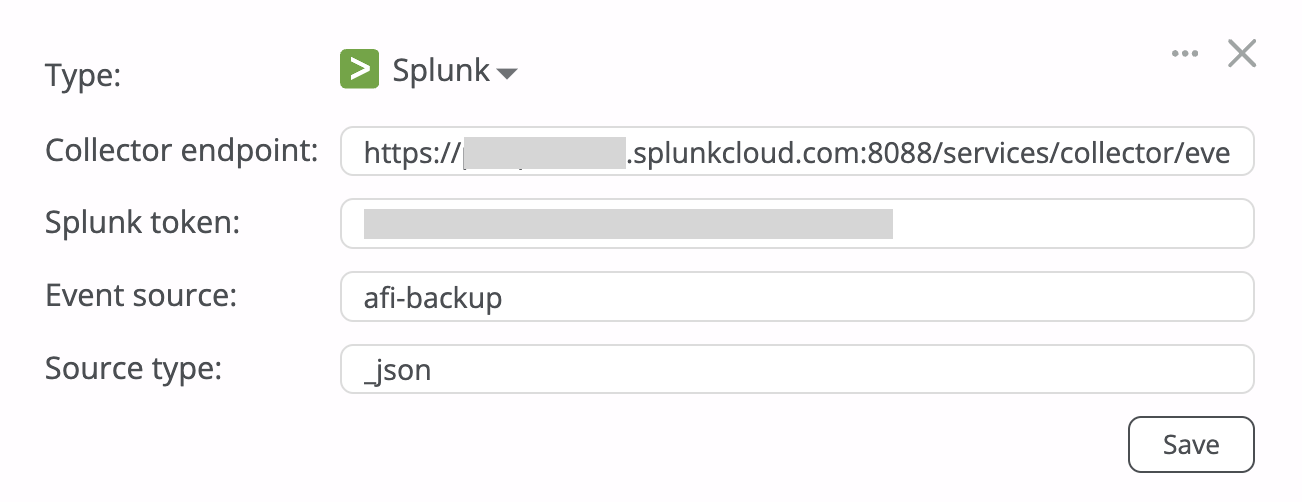
Step 3 - Create a Splunk channel on the Configuration → SIEM tab in the Afi portal with the following parameters:
- Collector endpoint: Splunk HEC endpoint
- Splunk token: Token from Step 2
- Event source: Event source from Step 2
- Source type:
_json
Please note that, by default, Splunk Cloud protects its HEC endpoints with a self-signed HTTPS certificate. Ensure that you have set up a custom SSL certificate issued by a commonly accepted certificate authority (CA) on the Splunk HEC endpoint.