Access model and Self-service¶
Afi Microsoft 365 backup has a flexible and granular role model that allows you to:
- delegate backup administration to a group of trusted users (referred to as Backup Operators);
- assign administrators with a limited access scope to manage and access specific resource groups;
- enable limited self-service access for Microsoft 365 tenant users.
Role model granularity allows an administrator to grant only a limited set of permissions tailored to their their own security and business needs. For example, the Backup Operator group can be configured to supervise backup progress and health, as well as perform data recovery operations per user request, but with no access to export backup data. For security reasons, self-service is disabled by default and administrators should explicitly enable it if needed.
Afi access model¶
Afi adopts a multi-tenant organizational and access model, allowing you to add and manage multiple tenants (e.g., Microsoft 365, Google Workspace) under a single Afi account (organization). The Afi access model is fully explicit and enables granular configuration of access at any level, whether for an entire organization, specific tenants, resource groups, or selected resources within a tenant, adhering to the principle of least privilege.
Organizational access settings are managed on the Configuration → Admins tab, granting access to the entire Afi organization and all tenants within it. Per-tenant access settings are managed on the Service → Settings → Access groups tab.
By default, an Afi organization account is created with a single administrator, the user who set up the account. Organization administrators can be added or removed on the Configuration → Admins tab (see the Organization Administrators group) and have full access to the organization and all its tenants. Organization-level settings are described in the following article, while this article focuses on tenant-level access settings specific to Microsoft 365 tenants.
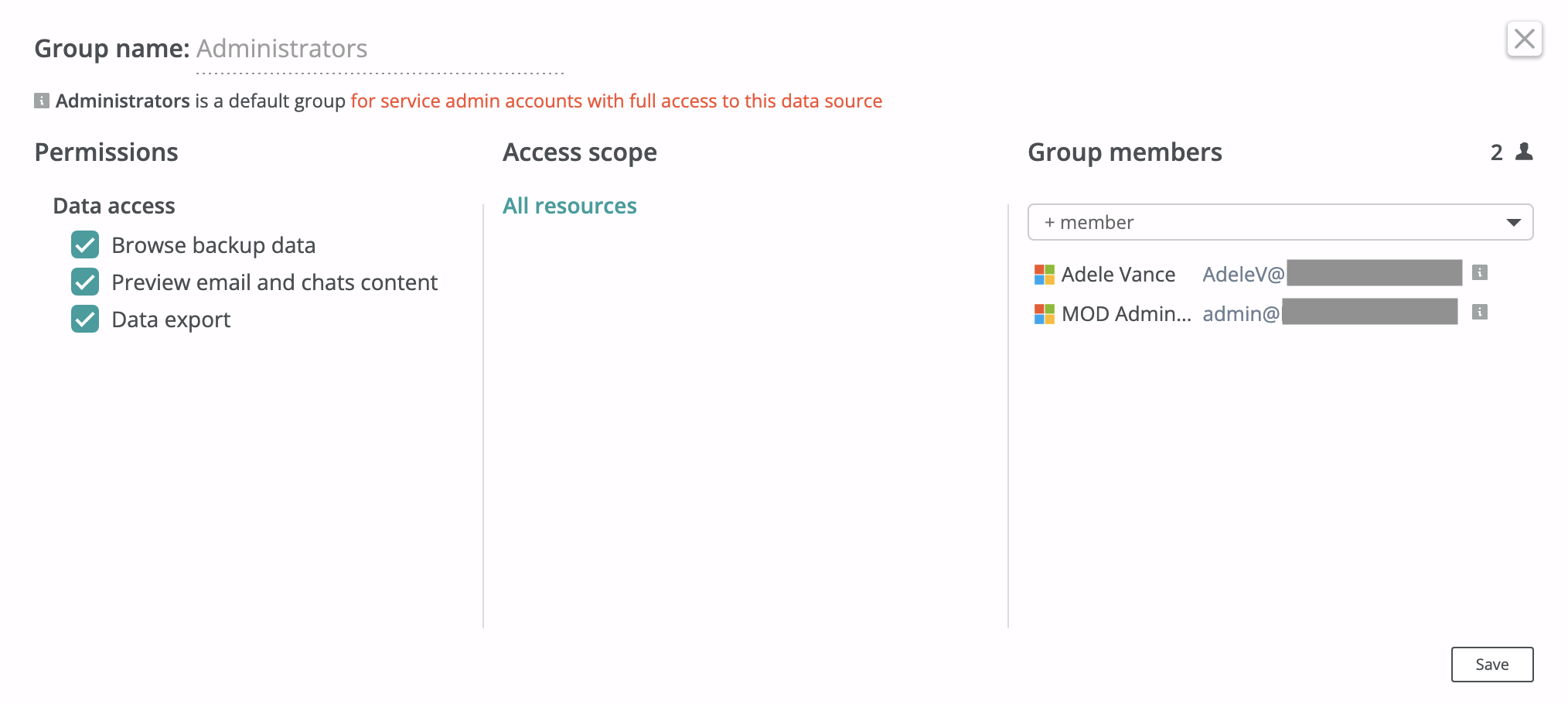
Administrators group¶
Tenant Administrators have full access to the tenant; however, even in a single-tenant Afi organization, they do not have access to organization-level settings such as licensing, organization-level access management, or the organization-level Afi audit log.
Info
Organization and tenant administrator access to backup data can be restricted either entirely by disabling the data browse permission for a tenant or partially by limiting email and chat content preview and/or data download.
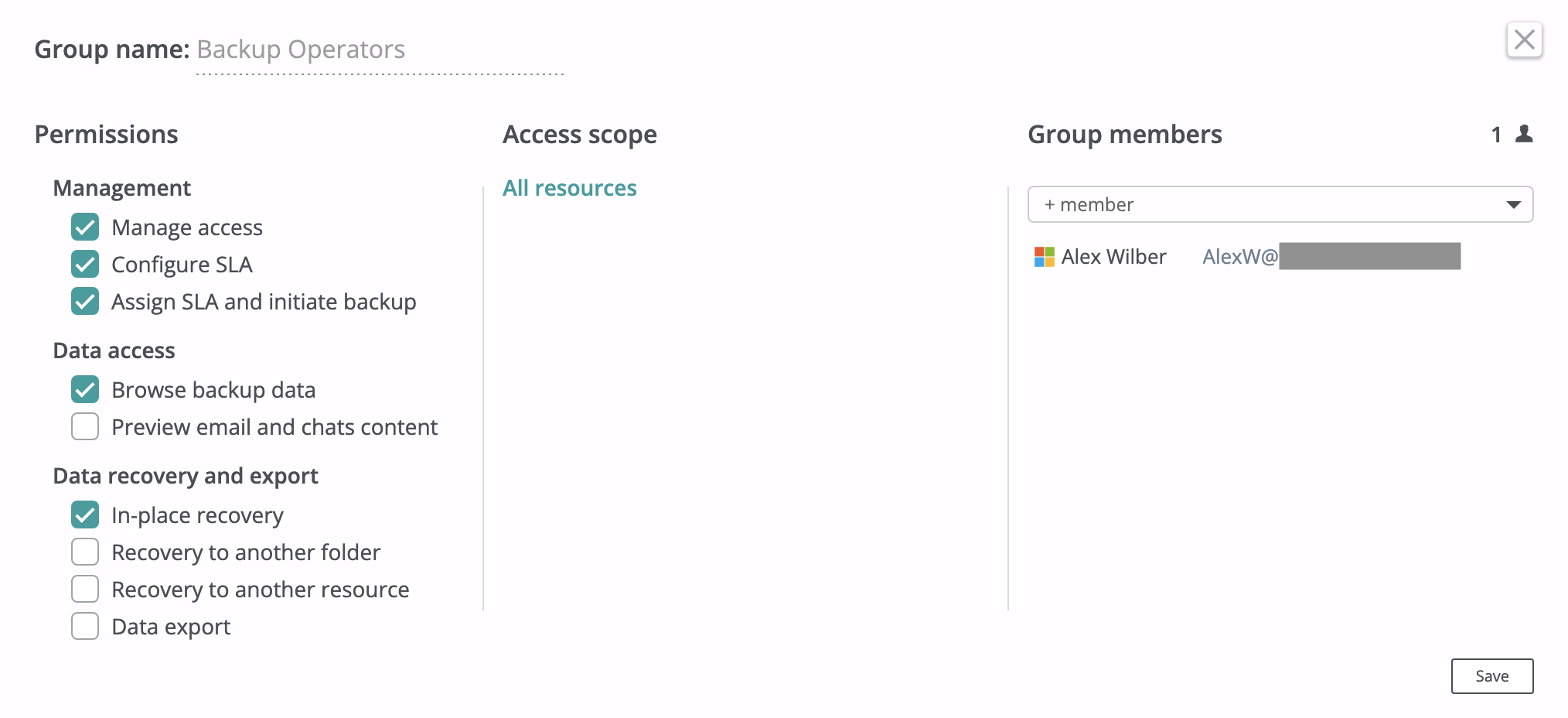
Backup operators group¶
The Backup Operators group is a default access group for each Afi tenant and can be used to provide limited tenant-wide access to backup management, data access, recovery, and export. The screenshot below shows the Backup Operators group with a single member who can manage backups and backup SLA policies, browse backup data, and run in-place recovery.
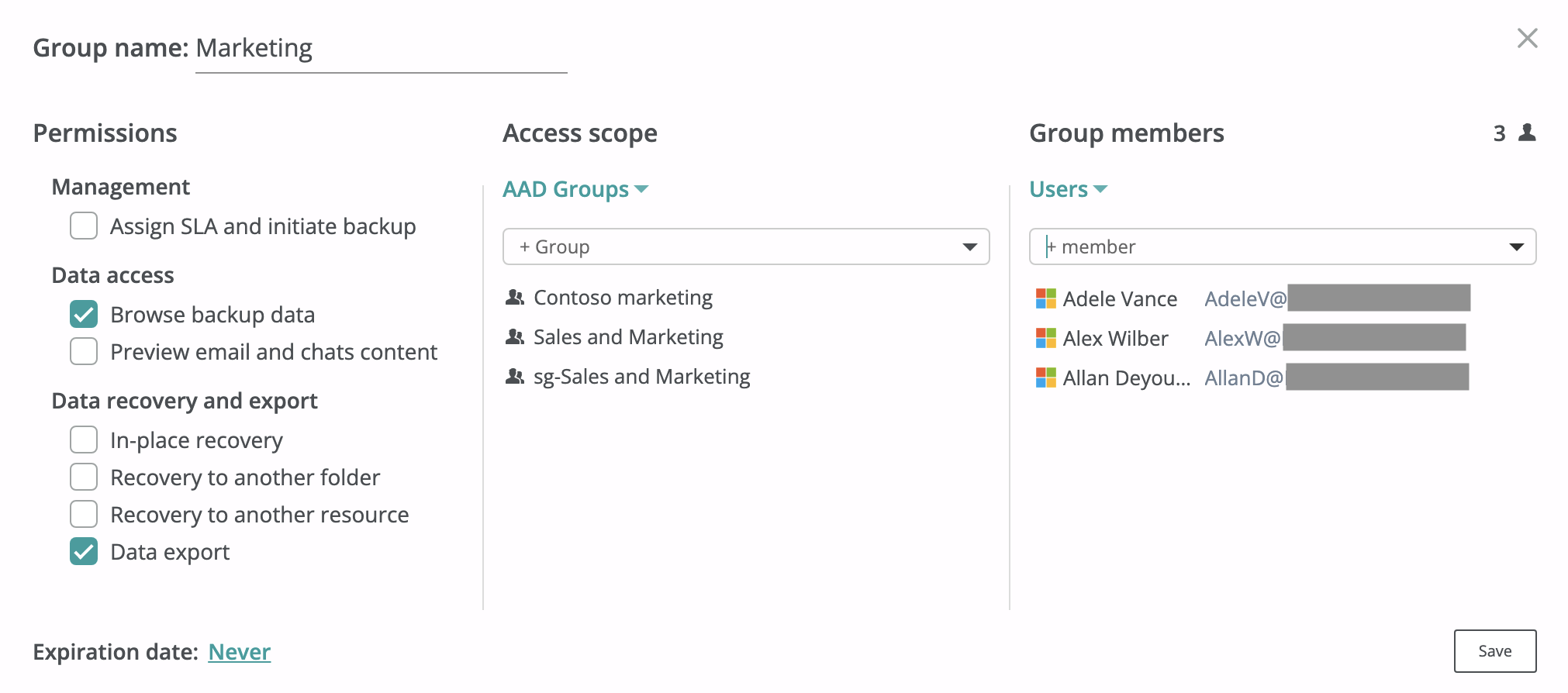
Custom access groups¶
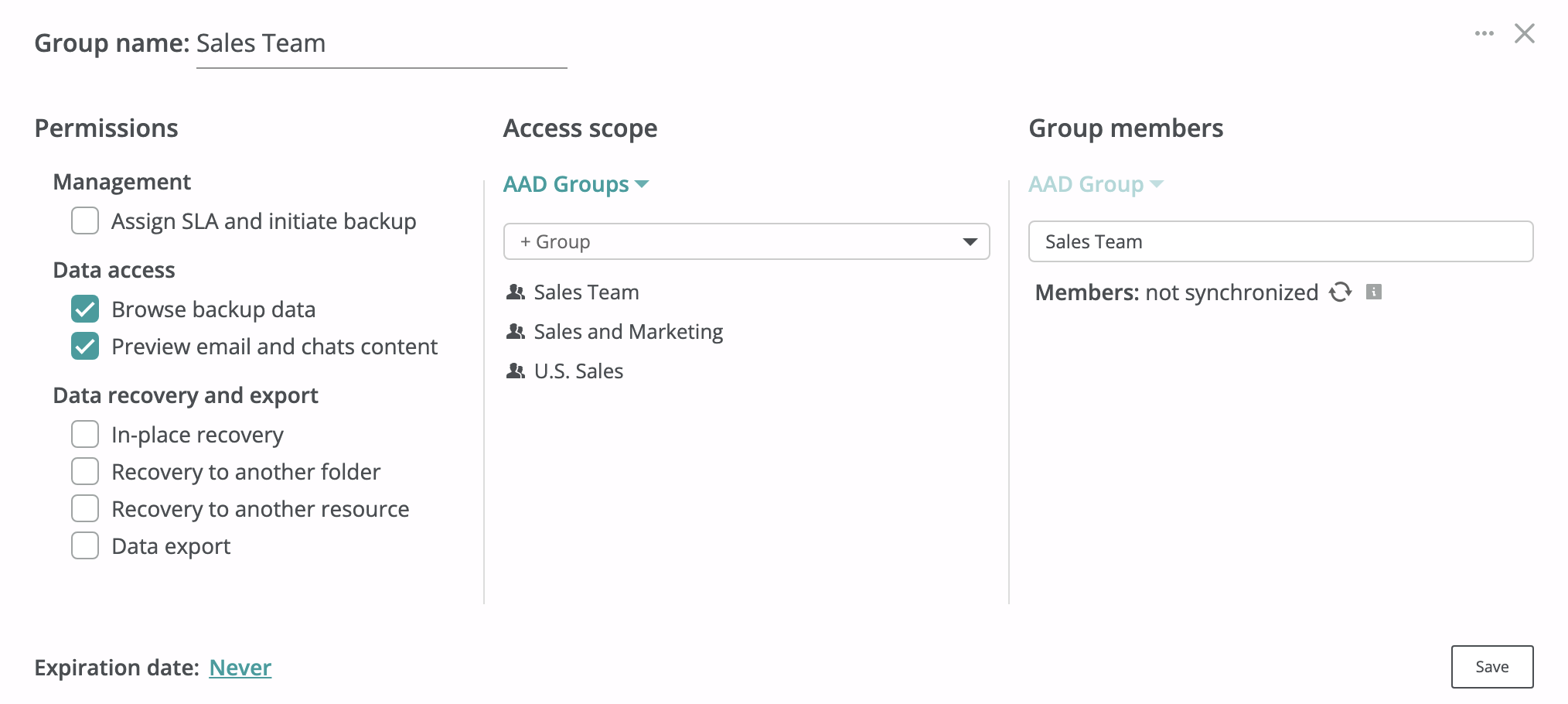
Custom access groups allow the creation of multiple administrator groups with limited permissions for a tenant, as well as grant granular access to resources that belong to a specific Azure Active Directory group or a manually selected set of resources. Access group members (users who are granted access through an access group) can either be configured manually by selecting users from the tenant scope or can be synchronized from an Azure Active Directory group inside the tenant. Custom access groups can also be configured to have a fixed lifetime, which is unlimited by default.
To configure a custom access group, please follow these steps:
- Go to the Service → Settings → Access groups tab.
- Click on the + Group button to add a new group, or select an existing group to edit its settings.
- In the prompted dialog, select the access scope (i.e., the resources that group members should have access to). The following access scopes are supported:
- All resources - Grants access to all resources and the corresponding settings within a tenant.
- Entra ID (AAD) Groups - Grants access to resources in the selected AAD groups.
- Self-service - Grants self-service access for selected users or members of the selected Google group to their own backups.
- Custom - Grants access to selected resources.
- Choose group members who will have access to the groups/resources within the access scope.
- Configure permissions to be granted to group members for the groups/resources within the access scope.
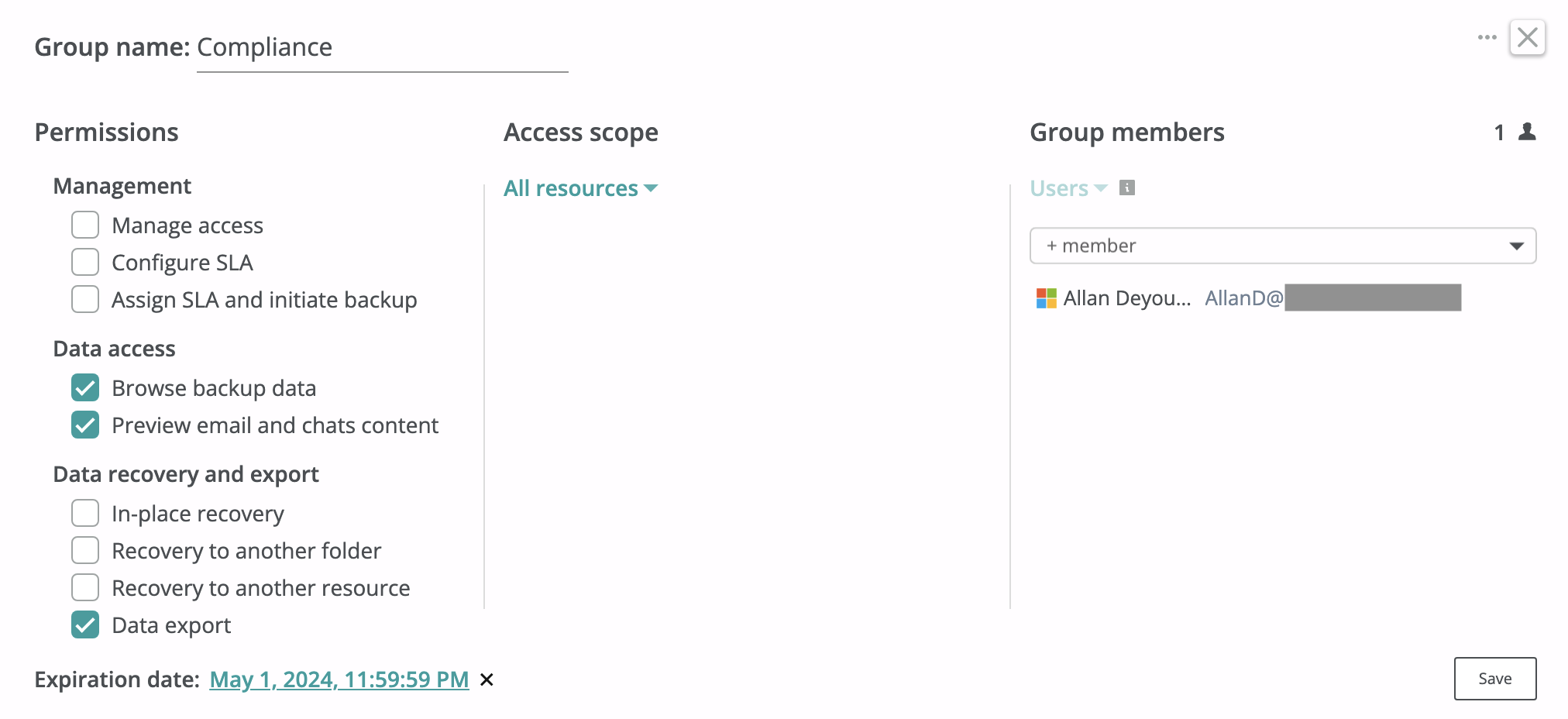
Access groups with limited lifetime¶
In some cases, it is useful to configure an access group with a limited lifespan to provide access only for a specified time period. For example, you might want to grant temporary access to a set of resources during an internal investigation or audit. The lifespan of an access group can be modified using the Expiration date control at the bottom of the access group configuration dialog.
Synchronizing access group members from an Entra ID (AAD) group¶
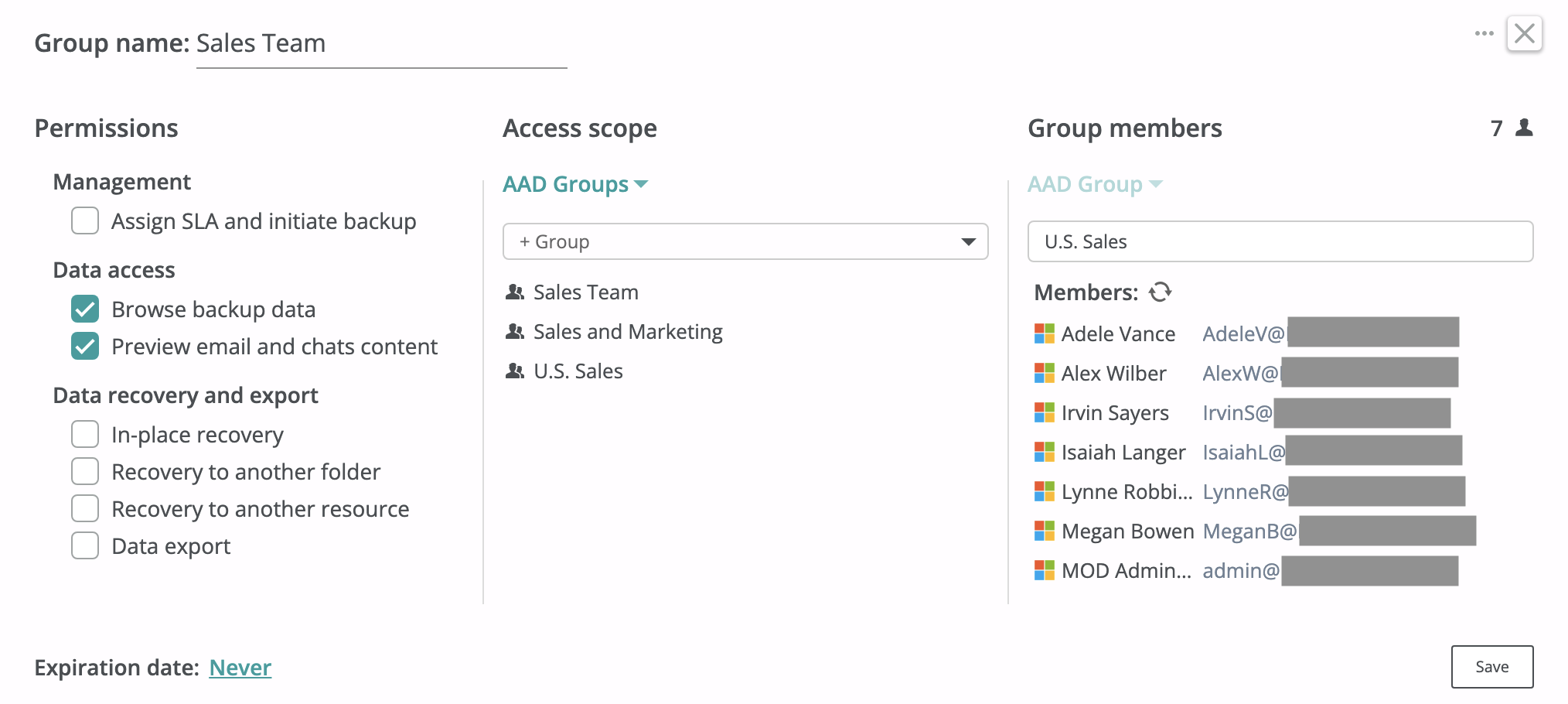
Access group members can be synchronized from an Entra ID group, thus enabling centralized access permissions management on the Entra ID side with changes propagation to Afi. To create an access group and grant access to members from an Azure Active Directory group, select the Entra ID (AAD) Group option in the dropdown in the Group members section and specify the group name. After such access group is created, you will need to trigger group members synchronization with Microsoft 365 for Afi to discover the group members (otherwise, members will be populated during a periodic synchronization performed by the service every 24 hours):
Once group members are synchronized from Microsoft 365, you will see them in the Group members section. Group membership changes are propagated to Afi once per 24 hours during periodic synchronizations with Microsoft 365.
Self-service access¶
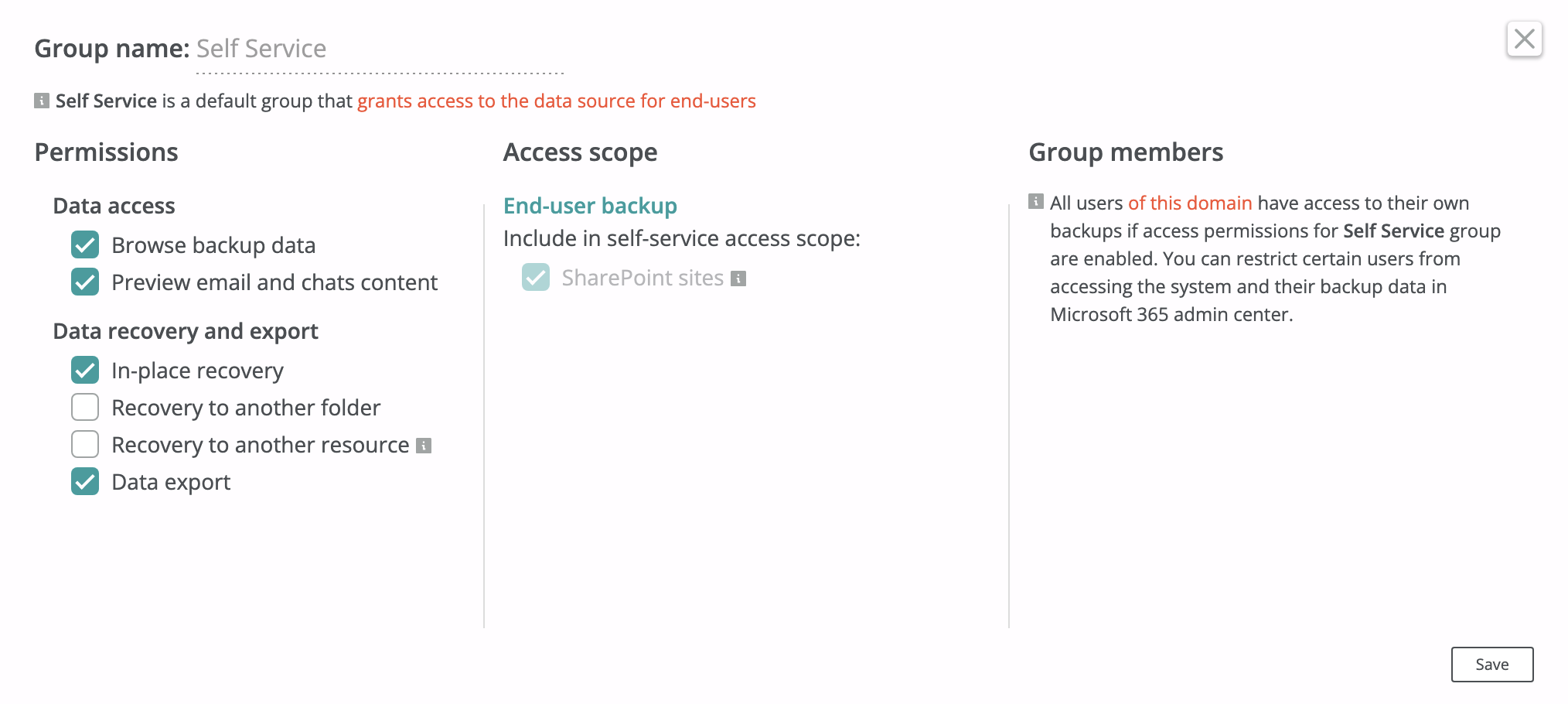
Afi allows organization/tenant administrators to enable self-service for end-users in a tenant so that they can access their own backups in the Afi portal and perform data export/recovery on their own, without involving the administrators. Self-service users can access the Afi portal via Microsoft SSO with the corresponding user accounts from the Microsoft 365 tenant. Actions performed by self-service users, including backup data access, search queries, export and recovery jobs, are audited in the same way as for administrators/access group operators.
Self-service access can also be extended to SharePoint as well as to Group/Team sites owned by a user (sites where a user has the Site Collection Administrator role on the Microsoft 365 side).
Info
Self-service access for Afi tenants is disabled by default.
Configuring self-service access for selected users and user groups¶
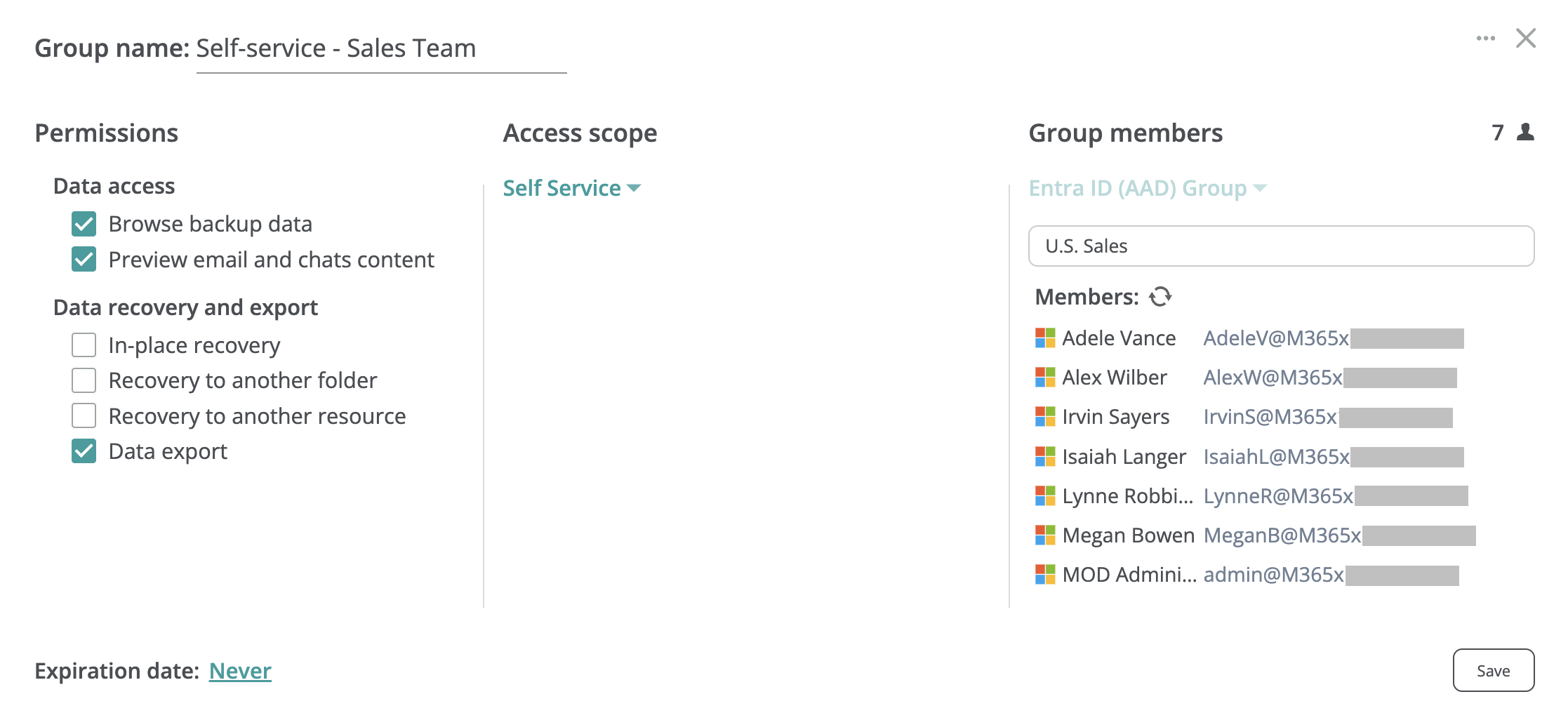
You can limit self-service access availability only to selected users or user groups in the Microsoft 365 tenant by creating a custom self-service access group. To do it, select the Self Service option in the Access scope section of the access group configuration dialog, then add users or an Entra ID group that will be granted self-service access in the Group members section.
Info
To grant self-service access for users in multiple Entra ID groups, please create an access group for each of these Entra ID groups.
When granting self-service access to their own backups for users in an Entra ID group, you can trigger an out-of-schedule group member synchronization as described in the section above.
To additionally restrict which Microsoft 365 users can see the Afi application launcher or log in to the Afi portal, please follow this guide.
Permissions explained¶
Access Group permissions explained¶
| Permission | Description |
|---|---|
| Manage access | Any access group member is able to change access settings within the tenant by creating new access groups or editing settings and members for existing ones. |
| Configure SLA | Any access group member is able to create, modify or delete backup SLA policies within the tenant on the Service → Settings → SLA tab. |
| Assign SLA and initiate backup | An access group member is able to assign backup SLA policies to resources within the group's access scope and configure auto-protection settings. |
| Browse backup data | An access group member is able to browse backup data for all backups within the group's access scope, but can't export the data or preview email and chats content without additional permissions. |
| Preview email and chats content | An access group member is able to preview email and chats content in all backups in the group's access scope. |
| In-place recovery | An access group member can trigger a recovery operation that restores all selected items (for example, emails/files) from a backup to the same resource and to the same paths where they were during a backup. This recovery mode should be used with caution as it will overwrite files if they have been changed since the time when the backup was done. |
| Recovery to another folder | An access group member is able to recover backup data to a separate folder/location inside a restore destination resource. This is the safest recovery option which guarantees that no data will be accidentally overwritten. |
| Recovery to another resource | An access group member is able to recover backup data to another resource. This option is enabled together with one of the following options: Recovery to another folder (default) or In-place recovery. |
| Data export | An access group member is able to download backup data from all backups in the group's access scope. |
Self-service permissions explained¶
| Permission | Description |
|---|---|
| Browse backup data | Any user in a tenant is able to browse their own backup data, but can't export the data or preview email and chats content without additional permissions. |
| Preview email and chats content | Any user in a tenant can preview email and chats content in their own backups. |
| Data export | Any user in a tenant is able to download data from their own backup. |
| In-place recovery | Any user in a tenant is able to recover their own data to its original location (recovery operation will reconstruct the original folder structure). This recovery mode should be used with caution as it will overwrite files if they have been changed since the time when the backup was done. |
| Recovery to another folder | Any user in a tenant is able to recover their own data from any selected backup snapshot (for example, a month ago) to a separate folder inside their own account. |
| Recovery to another resource | Any user in a tenant is able to recover their own data from any selected backup snapshot to another resource which they have access to on the Afi side (or to a new resource in case of a SharePoint site recovery to a new site). |